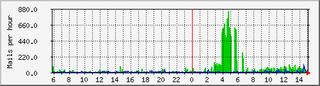
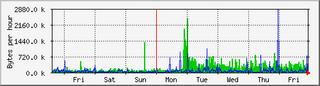
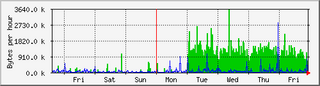
I had ranted before about the occasional trouble that I'm experiencing with the MacBook's wireless card.
The symptoms continue to occur: Typically at home (when the machine is in the same place and sits on my desk for extended amounts of time, sometimes days), typically during work hours, often when somebody else toys around with a network nearby, and only reproducible when I really can't use them. In other words: At least here, the MacBook isn't reliable accessing the wireless network during work hours, and I can't figure out anything in particular that I can do to trigger or avoid the problem.
(It's also clear that the problem isn't with the access point, as other machines here have no problem. Including a wifi enabled mobile phone and the Thinkpad. This is a genuine client issue, genuinely on the Mac.)
Searching around online has been a fool's errand and a time sink as well: While there are quite a few examples of similar problem (and while discussion threads often have a "yeah, I have the same problem"), none of them yield useful information about either causes or cures for the problem. The only consolation is, maybe, that the trouble seems to be common across the BSDs and Linux, and is certainly not just a Mac problem. (That consolation is rather immaterial, though -- we are, after all, talking about a problem with the (Atheros) wireless card that ships in these machines. By default.)
From what I've seen so far, this could be a Heisenbug anywhere between overheating (a bad fan?), a loose contact, a bit of conducting dust on the motherboard, a buggy driver, neighbors' secretly building and testing EMP weapons while cooking pancakes, or sun spot activcity -- even though some general instability (two panics and a freeze within two hours or so, anyone?) this morning points at hardware troubles close to the motherboard. (Oh, of course all is stable now that I'm sitting in elsewhere and have the laptop balanced on my leg -- overheating, after all?)
The next step is presumably AppleCare -- and I'll probably have to see how well my environment is back-ported to Linux on the Thinkpad, since travel and work won't wait for Apple to get it's act together.
PS: A crack that occurs on the right-hand palm rest, toward the front, on about every MacBook I've seen, doesn't count as quality hardware either.
PS2: I do like MacOS's, and the overall machine's usability. Really. But, please, not in a less stable environment than what Linux on the Thinkpad gave me. Till that machine's motherboard broke, that is. 2 weeks repair time there.
 First, as an all-time favorite, most corkscrews. The classical
First, as an all-time favorite, most corkscrews. The classical  Second, a recently-discovered stupidity, Samsonite's
Second, a recently-discovered stupidity, Samsonite's  Third, the keyboard in my trusty Dell laptop. A critical part of the mechanism is a relatively thin piece of tin that must be bent in the right way -- and, of course, is distorted over time, with all kinds of not so funny effects on my typing habits. The distortion effect is particularly strong with the shift and control keys, but can fortunately be fixed with a little bit of tinkering. The stupid assumption, though, that tin doesn't exhibit unelastic distortions, seems to have been commonplace in Dell hardware design for quite some time. I still remember some "workstations" which provided comfortable access to the PCI bus, but required re-bending some critical tin parts after the third exchange of a faulty PCI card.
Third, the keyboard in my trusty Dell laptop. A critical part of the mechanism is a relatively thin piece of tin that must be bent in the right way -- and, of course, is distorted over time, with all kinds of not so funny effects on my typing habits. The distortion effect is particularly strong with the shift and control keys, but can fortunately be fixed with a little bit of tinkering. The stupid assumption, though, that tin doesn't exhibit unelastic distortions, seems to have been commonplace in Dell hardware design for quite some time. I still remember some "workstations" which provided comfortable access to the PCI bus, but required re-bending some critical tin parts after the third exchange of a faulty PCI card.


